Dynamic Security
Logi Report Server administrators can change the security policy of a catalog at runtime, without having to edit the security in Logi Report Designer and publish the catalog again. This topic describes how you can create and apply dynamic security policies for catalogs using security files, which contain catalog security definitions.
Developer users can also use API to manage dynamic security.
This topic contains the following sections:
- Creating Security Files
- Creating Dynamic Security
- Changing the Security File of a Dynamic Security Policy
- Downloading Dynamic Security
- Applying Dynamic Security
Creating Security Files
The security files that you can use to create dynamic security on Logi Report Server are in XML format. You can create the security files by yourself, however, the best way to generate a security file is using Logi Report Designer.
A security file can contain security definitions of Record Level Security (RLS), Column Level Security (CLS), and Business View Security. For how to define RLS and CLS in an XML file, refer to Importing/Exporting Security Information from/to External XML Files in the Logi Report Designer Guide. As for the format of business view security, you can refer to the sample file DynamicSecurity.xml in <install_root>\help\samples\DynamicSecurity.
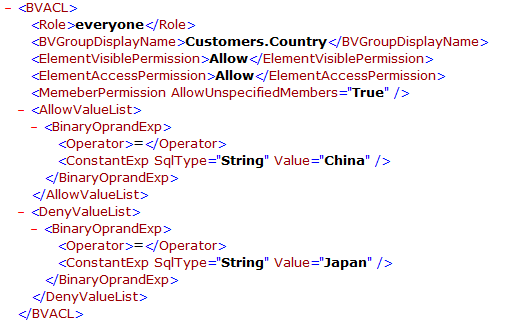
Suppose that you defined a business view security policy as follows:
| Principal | Element | Visible Permission | Access Permission | Allowed Set | Denied Set | Allow Unspecified Members |
|---|---|---|---|---|---|---|
| everyone | Customer.Country | Allow | Allow | China | Japan | True |
It is like this in the XML file:
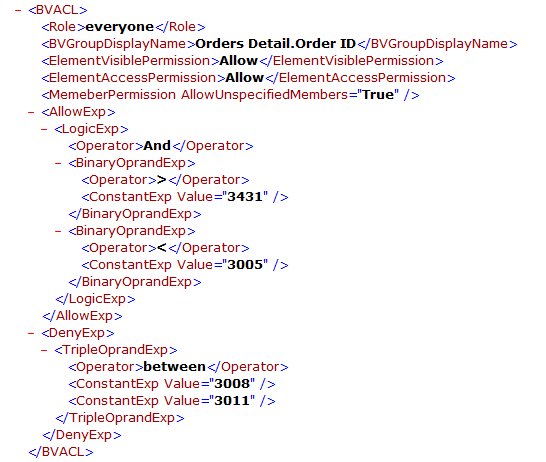
When you define the Allowed Set and Denied Set using expressions, for example:
| Principal | Element | Visible Permission | Access Permission | Allowed Set | Denied Set | Allow Unspecified Members |
|---|---|---|---|---|---|---|
| everyone | Orders Detail.Order ID | Allow | Allow | "Order ID" > 3431 And "Order ID" < 3005 | "Order ID" between 3008 and 3011 | True |
In the XML file, the business view security policy will be like this:
Creating Dynamic Security
To create a dynamic security policy, take these steps:
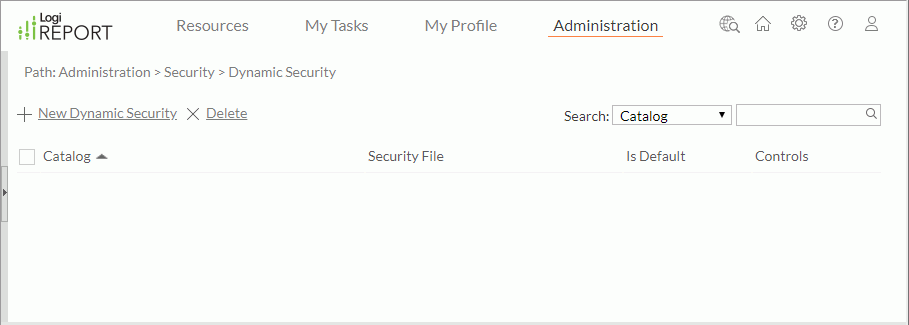
- On the system toolbar of the Server Console, navigate to Administration > Security > Dynamic Security. Server displays the Dynamic Security page.
- Select New Dynamic Security. Server displays the New Dynamic Security dialog box.
- Select Browse next to the Catalog box.
- Server displays the Select Catalog dialog box. Browse to the catalog you want to create dynamic security for.
- Select OK.
- Select Browse next to the Security File box.
- Select the security file based on which you want to create the dynamic security for the catalog.
- Select Open.
- Select OK to create the dynamic security. Server adds it to the dynamic security table.
One catalog can have several dynamic security policies. In this case, you can choose one of them as the default dynamic security of the catalog. To do this, select false in the Is Default column for the dynamic security.
If you want to remove a dynamic security policy, select it in the dynamic security table, then select Delete. You can delete multiple dynamic security policies at a time.
The following table describes the options in the Dynamic Security page:
| Option | Description |
|---|---|
| New Dynamic Security | Select to create a dynamic security in the New Dynamic Security dialog box. |
| Delete | Select to delete the selected dynamic security. |
| Search | Search for specific dynamic security.
|
| Dynamic security table | |
| Checkbox | Select or clear a dynamic security. Select the checkbox on the column header to select all the dynamic security. |
| Catalog | Catalog for which a dynamic security is, with the full resource path, for example, /Public Reports/SampleReports/SampleReports.cat. You can select the column header to sort the column. |
| Security File | Name of the catalog security file for a dynamic security. You can select the column header to sort the column. |
| Is Default |
Server shows whether a dynamic security is the default. The value is editable. Select false to set a dynamic security as the default. For a catalog, you can set only one dynamic security to true, and the latest setting takes effect. You can select the column header to sort the column. |
| Controls | Control the dynamic security.
|
Changing the Security File of a Dynamic Security Policy
You can modify the security file based on which the dynamic security policy of a catalog is. To do this, select Upload in the Controls column for the dynamic security. Server displays the Upload Dynamic Security dialog box. Select another security file to create the dynamic security for the catalog.
Downloading Dynamic Security
You can download the dynamic security you defined on Server to a file. To do this, select Download in the Controls column for the dynamic security. Server downloads it to your drive. You can then modify the security definitions in the file. After editing, you can upload the file to a dynamic security policy to change the security definitions in the policy.
Applying Dynamic Security
After you specify a default dynamic security policy for a catalog, when running reports, dashboards, or analysis templates which use the catalog, no matter interactive, on-demand, or scheduled, Logi Report will always try to load the dynamic security for the catalog before running and try to use the security defined in the security file on which the dynamic security is based to replace the catalog security.
- For business view
For each given principal and business view, if there is security definition in the security file, it will replace the whole security definition for this principal on this business view.If the security file mentions a business view element, but the element is not in the catalog, Server will ignore the security file.
- For security entry
For a given principal and a security entry, if there is CLS definition in the security file, it will replace the CLS in the catalog security. If there is RLS definition in the file, it will replace the RLS in the catalog security.
If there is no default dynamic security specified for a catalog, the security definitions created in the catalog at design time will apply.
 Previous Topic
Previous Topic
 Back to top
Back to top in the text box to start the search.
in the text box to start the search.